By Koen Van Impe December 8, 2023
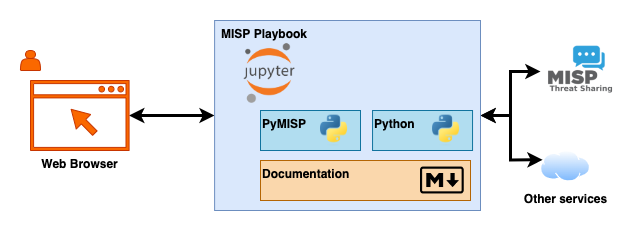
Current state of the MISP playbooks
The MISP playbooks at https://github.com/MISP/misp-playbooks address common use-cases encountered by SOCs, CSIRTs or CTI teams to detect, react and analyse intelligence received by MISP. The project started early 2023 and as we’re now ending the year it’s time to look back at its current state and get an early glimpse of the future features.
But before we do that, maybe it’s good to first remind us what the MISP playbooks are about.
Introduction
A recurring problem with playbooks, standard operation procedures or workflows is that documentation (why, where, when, who) and commands (activities, the what) often reside in different places. Version tracking and sharing playbooks with others can also be a nightmare. That’s where Jupyter notebook jump in. Jupyter notebooks are an interactive environment where users can write and execute computer code and combine the code with documentation (in Markdown). For the MISP playbooks we extend this with PyMISP, the Python library for MISP. As a user, you only need a web browser to interact with these playbooks. The MISP playbooks are also in JSON format so you can store them in a versioning system, track their changes and share them with others.
The GitHub repository has guidelines to help you with building and maintaining your own playbooks and technical documentation to setup your environment. For those that are impatient: there’s a guide to quickly set it up on a Kali VM (or basically any Linux VM).
The structure of the playbooks is also explained, along with a basic example. There’s even a small slidedeck of a presentation given for the FIRST Automation SIG.
Current state
Commits
Since the start of the project there have been 30 commits, resulting in 15 MISP playbooks and guidance and technical documentation on how to setup an environment for MISP playbooks.
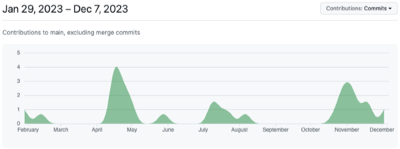
Issues
The GitHub issue tracker is used to track the development of the playbooks. Basically each playbook corresponds with an issue. The issue tracker is also your best choice to request a new playbook (via the New MISP playbook proposal template). So far there are 50 issues created, with 20 issues already closed.
![]()
Playbooks
The current MISP playbooks cover the needs of MISP users and MISP administrators. For the former there are playbooks to
- Deal with malware investigations
- Do OSINT investigations
- Use the MISP features to search for specific pieces of information
- Become better acquainted with the MISP features
- Use the playbooks to deal with phishing incidents
- Create or update a MISP event with information from a phishing incident with a link (1)
- Use MISP for CTI work
- Threat actor profiling (26)
For the MISP administrators there are playbooks to
There is also a skeleton playbook that is used to start a new playbook.
Activities in 2023
If you review the issues you’ll notice that most are labelled with playbook:activity. This label is used to group the work in different phases of development. In the first year, the focus was on
Activity 1 : Creating a first set of playbooks and documentation guidelines
- Four playbooks are published, in addition to a skeleton playbook.
- Documentation guidelines to help users jump on board and start using the playbooks.
Activity 2 : A second set of playbooks with technical documentation
- An additional six playbooks are published, aimed towards MISP users and administrators.
- Technical documentation to setup an environment to use the playbooks.
Activity 3 : Advanced playbooks
- Six (22 soon to be published) more advanced playbooks are published.
Moving forward
The GitHub repository also holds the work that is foreseen for 2024. What can you expect for the future?
Activity 4: MISP workflow integration, Elasticsearch, MDTI and support for curation
- First explore the options to integrate the MISP playbooks with MISP workflows
- Playbooks that query Elasticsearch for indicators from MISP. The playbook adds sightings and creates a summary (5)
- Interaction with the Microsoft Defender Threat Intelligence (MDTI) API (44)
- Search for JARM fingerprints (19)
- Document the playbooks in JSON (48)
- Support threat intelligence curation (30, 23 and 21)
Activity 5: Timesketch, conversions with CACAO and Microsoft Sentinel
- Following the Elasticsearch playbook, a playbook that has similar features but now with Timesketch integration (6)
- Investigate if there can be translations between MISP playbooks and CACAO playbooks
- A CACAO playbook (v2) is a workflow for security orchestration containing a set of steps to be performed based on a logical process. There are overlaps between CACAO and MISP playbooks, so a translation / conversion is only the next logical step (49)
- Following the integration between MISP and Microsoft Sentinel, playbooks that create MISP events based on the data in Sentinel incidents (34)
- Additional playbooks to deal with malware and phishing (URLs) (16, 14 and 4)
Activity 6: Scheduled playbooks, timelines,
- Traditionally playbooks are executed based on a human trigger.
- In this activity the options are explored to parametrise and schedule the execution of MISP playbooks (47)
- Create a timeline based on different MISP events or search queries (28)
- Additional playbooks to support threat intelligence curation (24 and 50)
- Try to integrate the suggestions from “Getting Started with ChatGPT and Jupyter Notebook " in MISP playbooks (38)
- Playbooks to create filter lists (18) and do domain pivoting (17)
Conclusion
As you can observe from the above, there’s still quite some work ahead. Important is that the list of playbooks to develop is only a list of suggestions. If you have a good idea for a playbook or if you find yourself doing the same activities over and over again, then document the steps and request a new MISP playbook to be developped for it.




