By Koen Van Impe August 26, 2023
MISP to Microsoft Sentinel integration
Introduction
The MISP to Microsoft Sentinel integration allows you to upload indicators from MISP to Microsoft Sentinel. It relies on PyMISP to get indicators from MISP and an Azure App to connect to Sentinel.
Graph API and Upload Indicators API
In April 2023 the MISP to Azure Sentinel integration was covered. This integration used the Microsoft Graph API. Since then, Microsoft deprecated the Graph API, and preferred new integrations to rely on the Upload Indicators API. The new MISP to Microsoft (previously Azure) Sentinel or misp2sentinel does just that, it
- Supports integration with the old Graph API, but most importantly,
- It supports the new, and preferred, Upload Indicators API.
To get started you need
- An Azure App, with read and write permissions on your Microsoft Sentinel workspace and a threat intelligence Data Connector;
- A MISP API key to pull data out of MISP;
- The misp2sentinel code in a Python3 virtual environment or as an Azure Function, with the necessary libraries such as MISP-STIX.
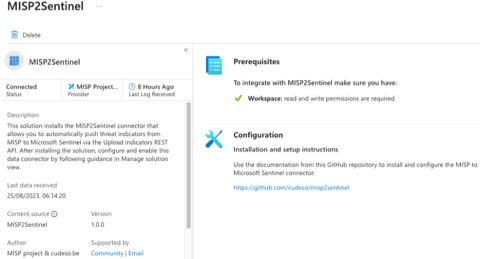
Microsoft Azure Market Place
The misp2sentinel solution is in the Market Place or Microsoft Sentinel Content Hub with a corresponding data connector. Note that enabling the solution in Azure isn’t sufficient to sync indicators. You still need to setup the Python environment or use the Azure Function.
Python environment
The setup of the Python virtual environment is described in the README. Basically you need to clone the repository, setup the Python3 environment, install the necessary libraries and then update the configuration file.
In general this should not take longer than 10 minutes.
Azure Function
Next to a “traditional” Python environment installation, there is an option to do the integration via an Azure Function. The code is contributed by Infernux and provides you a great approach to have the integration running directly within Sentinel.
STIX
The Upload Indicators API of Microsoft is STIX based. STIX is a structured language for describing threat information to make sharing information between systems easier. This integration relies on the MISP-STIX library to handle the conversion between MISP and STIX.
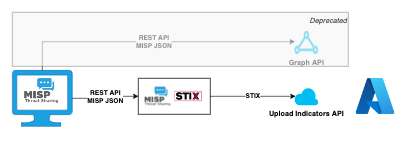
From a functional point of view, all indicators that can be synchronised via the Graph API, can be synchronised via the Upload Indicators API. There are some features missing in the STIX implementation of Sentinel and as a result some context information (identity, attack patterns) is lost. But it is only a matter of time before these are implemented on the Sentinel side, after which you can fully benefit from the STIX conversion.
Sentinel Workspaces
In addition to the change to STIX, the new API also supports Sentinel Workspaces. This means you can send indicators to just one workspace, instead of pushing them globally.
Configuration changes
If you used the old Graph API version before then it’s worth having a look at the new configuration settings and requirements before upgrading.
GitHub repository
The code and documentation is at https://github.com/cudeso/misp2sentinel.
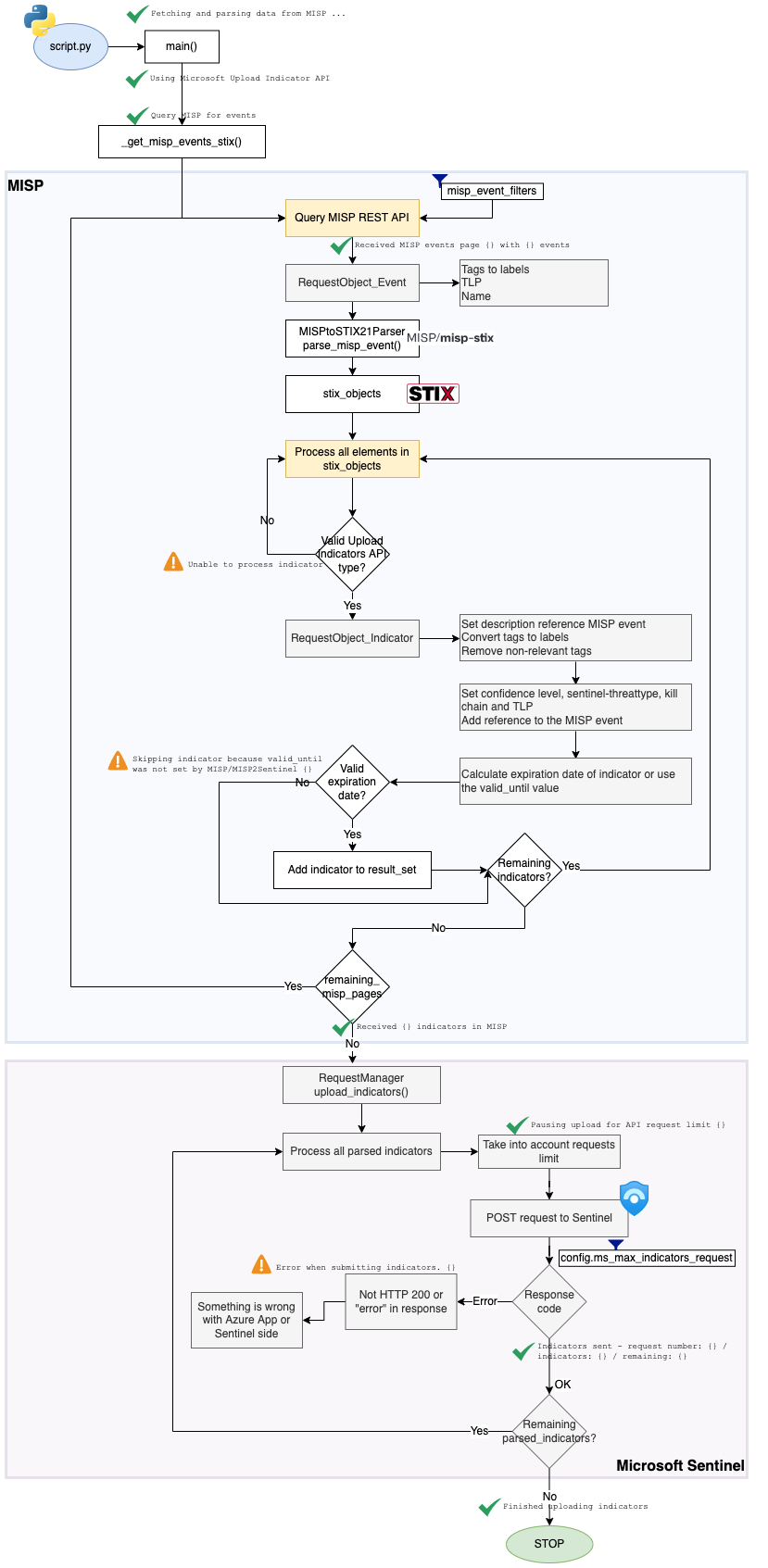
Workflow
The ‘workflow’ of the integration is outlined in this diagram.